If you are migrating policy agent configuration from a version earlier than 12.0.0, do take note that you need to fill in Realm and Application in Policy Client Service section.
The following is the release note from OpenAM 12.0.0. It applies to version 13.x.x.
Now, OpenAM 13.5 behaves a little different from 12. (I'm not too sure of v13.0 as I skip that version totally)
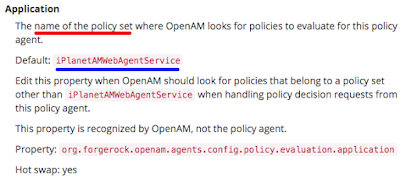
In OpenAM 13.5, there is this concept of Policy Set whereby you need to key in a Policy Set ID and Policy Set Name. Policy Set ID is hidden most of the times after initial setup.
However, when you configure Policy Agent and you need to fill in the Realm and Application, you need to be careful.
Application refers to Policy Set ID, not Policy Set Name.
Confusing isn't it, since Policy Set ID is hidden unless one clicks on the Details tab?
It's also a bit confusing that one section of the console keeps using Policy Set and Policies, while the other section keeps using Application, when they are supposed to mean the same thing.
Documentation might help a little, except they contradict slightly.
Anyway, what will you observe if you hit into this issue?
On the frontend, this is what will be thrown:
This is especially not helpful. Reminds me of SiteMinder integration. :) One will be shown the same Internal Server Error for every possible error that can occur. Ha!
On the backend, this is what is being captured in the logs:
org.forgerock.audit.events.handlers.writers.RotatableWriter:08/23/2016 11:00:33:052 AM SGT: Thread[CsvHandler,5,main]: TransactionId[17960893-bd4e-4da2-ab8b-369a360d5a28-58]
Actually writing to file: "17960893-bd4e-4da2-ab8b-369a360d5a28-736","2016-08-23T03:00:33.051Z","AM-ACCESS-OUTCOME","17960893-bd4e-4da2-ab8b-369a360d5a28-734","id=oneaccess,ou=agent,dc=azlabs,dc=sg","[""9b54bd2abc7e586601""]","idp.azlabs.sg","443","192.168.XX.XX","41971","PLL","REQUEST_GET_RESOURCE_RESULTS",,"true","POST","https://XXX.XXX.sg/openam/policyservice","{}","{""accept"":[""text/xml""],""host"":[""XXX.XXX.sg""]}","{""amlbcookie"":""01""}",,"FAILED",,"{""reason"":""Evaluation error.\nUnable to retrieve application under realm /.\nUnable to retrieve application under realm /.""}","17","MILLISECONDS","Policy","/"
A little bit of getting used to. Otherwise, we're good to go for OpenAM 13.5! :)
.