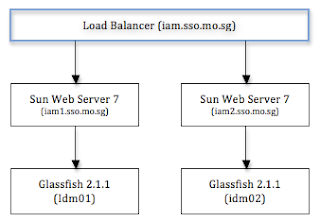
Directory.
We know that Microsoft Active Directory is able to detect first-time-login, password expired, account locked, account disabled etc ...
However, by using the in-built Active Directory Authentication module in OpenSSO, it keeps displaying the same error "Invalid credentials" whenever any of the errors is encountered. This confuses the users a lot. It also gives administrator wrong impression of what exactly is the error.
If a manual search is performed, the following is what we get:
bash-3.00# ldapsearch -h 192.168.131.50 -p 389 -D "cn=cclow,cn=users,dc=central,dc=sg,dc=sun" -b "dc=central,dc=sg,dc=sun" -s sub "objectclass=*"
Enter bind password:
ldap_simple_bind: Invalid credentials
ldap_simple_bind: additional info: 80090308: LdapErr: DSID-0C0903AA, comment: AcceptSecurityContext error, data 773, v1771
bash-3.00# ldapsearch -h 192.168.131.50 -p 389 -D "cn=cclow,cn=users,dc=central,dc=sg,dc=sun" -b "dc=central,dc=sg,dc=sun" -s sub "objectclass=*"
Enter bind password:
ldap_simple_bind: Invalid credentials
ldap_simple_bind: additional info: 80090308: LdapErr: DSID-0C0903AA, comment: AcceptSecurityContext error, data 533, v1771
Microsoft Active Directory has this habit of sending back error messages in 2 lines. The 1st contains what I call it General Error Message. The 2nd will contain the Actual Error Message ("additional info").
In this 2nd line, you need to tokenizes the message to grab the part that contains ", data xxx,". This will give you the Exact Error Message.
ldap_simple_bind: additional info: 80090308: LdapErr: DSID-0C0903AA, comment: AcceptSecurityContext error, data 533, v1771
So we went ahead to develop our own custom Active Directory Authentication module, and we have the following mapping:
public static final String ERROR_FIRSTTIME = "773";
public static final String ERROR_PASSWORDEXPIRED = "532";
public static final String ERROR_ACCOUNTLOCKED = "775";
public static final String ERROR_ACCOUNTDISABLED = "533";
public static final String ERROR_ACCOUNTEXPIRED = "701";
.